Adoption of IoT in 2020 and 4 Lessons we can learn from it
A decade ago, the internet only connected to computers and people. However, the Internet of Things or IoT came along and changed the world we know. It brought together all kinds of connected devices into a global network. From smart cars to smart cities and smart homes, IoT turned everything around us into a smart device.
While the Internet of Things is believed to bring a boom in the job market, the lack of skills is considered as the biggest barrier in implementing this technology. In order to reap the benefits of IoT, you need to equip yourself with the proper knowledge and be industry ready. If you’ve felt yourself lost and want to learn more about this increasingly connected world, you’ve landed on the right page.
This blog will discuss the basics of IoT, its evolution, adoption and how IoT is changing the world. It will primarily cover:
What is the Internet of Things (IoT)?
- IoT Evolution
- IoT Architecture
- Current industry standing and future adoption
- Areas of adoption and the lessons to learn
What is IoT?
IoT is a network of computing devices, machines, objects, people or animals that are interconnected to share data without the need for human intervention. Each device, machine, person, etc. on the network has a chip, sensor or an IP address assigned that enables it to transfer data over the network.
Increasingly, organizations in various industries have started using IoT to streamline their operation, improve their customer service and increase the value of their business.
History of IoT:
The term ‘internet of things’ was first used by Kevin Ashton in a presentation that he made to Proctor and Gamble in 1999. Though the idea of adding intelligence to objects was discussed since the 1980s, Ashton was the first to mention ‘Internet of Things’ in the presentation where he wanted to bring radio frequency identification (RFID) to the attention of Proctor and Gamble’s senior management.
The progress on IoT was slow up until very late because the required technology wasn’t ready yet. Some of the issues were solved as processors became cheap and power-frugal, along with the increasing penetration of broadband internet and availability of cellular and wireless networking.
Evolving from machine-to-machine communication, IoT has now come a long way connecting billion of smart devices and people who can now collect and share data. IoT is also a natural extension of SCADA, which is a category of a software application program for process control. SCADA systems are responsible for gathering data in real time from remote locations and feeding it into a system that has SCADA software installed. The late generation SCADA systems can be thought of as the first generation IoT systems.
The IoT ecosystem, however, boomed in mid-2010 when China made IoT a strategic priority in its five-year plan. Since then, IoT adoption and its applications have skyrocketed to the extent that it has paved the way for a potential fourth industrial revolution. Experts also predict that half of the businesses will run on IoT by 2020.

IoT Architecture:
You might have understood by now that IoT is more than just internet-connected devices. It is the technology that builds systems capable of sensing and responding to stimuli without any human intervention.
Below, we present the IoT Architecture that comprises of four stages:
Stage 1: In the content of IoT, a device must be equipped with sensors and actuators, so that it can process, send, or receive, signals.
Stage 2: The data sent from the sensors and actuators are analog which needs to be converted into digital streams for processing. The Data Acquisition systems are responsible for aggregation and conversion of data.
Stage 3: After the data is aggregated and digitized, the Edge Analytics comes in to perform further processing on the data as it enters the data center.
Stage 4: Data that needs more in-depth processing gets forwarded to physical data centers or cloud-based systems.
Current industry standing and future adoption:
The IoT industry is in its infancy as most of the products don’t always easily connect and there are still some significant security issues with it.
However, the industry is growing, and things are improving at an exponential rate. Analysts at Gartner calculated that there were over 8.4 billion IoT devices in use in 2017. This indicates an increase of 31 percent over the previous stats showed for 2016. More than half of these devices were consumer products like smart speakers and smart TVs. Smart electric meters and commercial security cameras were the most used enterprises IoT devices as per the Gartner report.
Related Blog: Why Your Business Adopt IoT
In 2017, the total spending on IoT endpoints and services reached a whopping 2 trillion dollars, with 2/3rd coming from China, Europe, and North America.
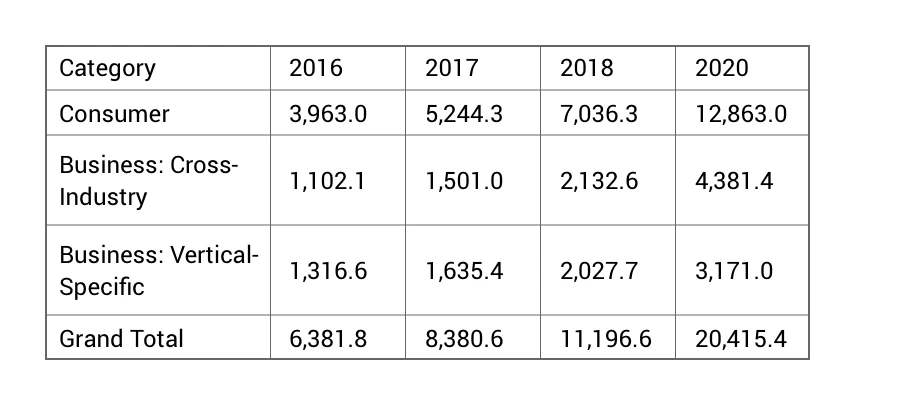
Gartner also estimated that the total number of IoT devices would likely reach 20.4 billion by 2020. Data from Juniper Research, however, suggests that over 17 billion more IoT connected devices will be deployed globally by 2020, which will take the numbers to around 38 billion in the next five years.
A report on the Internet of Things from the firm also warned that despite the UK’s government recent report to urge retailers to embrace IoT devices, businesses need to have the right system to deploy IoT and handle the data it produces. Analyst and research author Steffen Sorrel added that.
Cisco also decided to enter the arena of IoT with a new system about smart city infrastructure. Currently, various IoT products are coming from Cisco IoT System, ranging from mass-transit WiFi access points, security cameras and 4G modules targeted to turn data into action.
A word on IoT security and Privacy:
The biggest issue with IoT is security. The sensors deployed in the devices collect extremely sensitive data in many cases – smart home or smart TV for instance – that needs to be kept secure. So far, the IoT track record for security has not been very impressive. Software flaws, even in old and used software, are discovered regularly which puts questions on where IoT is heading vis a vis security. A study revealed that 84 percent of organizations have experienced an IoT-related security breach.
Hackers have been targeting IoT devices including webcams and routers for a long time which means these devices are constantly at risk. This is an inherent lack of security in the devices that make them easy targets for hackers. Such flaws have left smart home equipment like ovens and refrigerators open to hackers. Researchers found that there are around a hundred thousand webcams that could be easily hacked while some smartwatches were also found containing security vulnerabilities. The flaws in the smartwatch allow hackers to track location, eavesdrop on conversations of the person wearing the watch.
The security threats equally apply to business where the stakes are much higher. There is always a risk of a potential attack from hackers as you connect industrial machinery to IoT networks. A single attack or industrial espionage can deal a mighty blow to any business. This makes network isolation, the security of sensors and data encryption necessities for businesses. The current state of IoT technology and lack of consistent security planning across companies makes IoT security a challenging task.
IoT privacy:
The privacy of IoT is also a headache with all those sensors collecting personal data about you, your home, or business. Consider the smart home for instance. It knows your wake up time, which radio station or TV station you listen to or watch (thanks to smart speakers and smart TV), information about the food you eat (smart oven or refrigerator). While the companies make a profit by selling you all the IoT devices, there is also a possibility that they sell your data to companies who need it.
Not all smart home businesses will build their business model around collecting customers data and selling it, but no one knows how they use it. There is also a possibility to use bits of data and create a detailed picture of you based on that data. A researcher found that based on home’s energy consumption, CO and CO2 levels, humidity and temperature, it is possible to work out what someone had for dinner.
The IoT and cyberwarfare:
Since IoT devices bridge digital devices with the physical world, any security lapse can have dire consequences in real-world. For example, if the sensors that control the temperature in a power station gets hacked, that could be a catastrophic event for the entire region. Similarly, getting an autonomous car hacked can entail perilous consequences for you or anyone else driving on the road.
A US intelligence community has already warned that their adversaries may have the potential to threaten its infrastructure as well as the connection or consumer devices such as thermostats, cookers, and cameras. They have also warned that these devices can be used to spy on citizens. Adding critical infrastructures like dams, bridges, and electricity can also be potential targets that make the security of connected devices even more vital.
Four lessons to learn:
The deployment of IoT devices so far taught us some important lessons. This section covers those lessons that need to be kept in mind for future IoT adoption.
1.Improvements in IoT infrastructure:
There is no denying the fact that the proliferation of IoT and the growth of smart devices will produce many opportunities for businesses to grow; however, it will also put enormous pressure on the IoT infrastructure. As the huge data travel back and forth between sensors, endpoints and data centers, or cloud, the current IoT infrastructure may not withstand it. Some of the concerns regarding enterprise IT infrastructure include:
- Need for faster and high-volume data storage systems:
IoT data is accumulated, processed and sent by sensors from various devices within a network. Most of this data will be preserved and analyzed to generate useful insights which are sent back to the central terminal. This process requires high capacity, faster storage and memory processing technologies. Object storage is recommended for IoT storage as it can accommodate a large number of files into storage devices. For this reason, most of the cloud service providers use object storage which makes cloud-integrated storage ideal for IoT data.
- Need for networks with high bandwidth and low latency:
Along with faster and high capacity storage systems, there is also a need for agile network infrastructure. For large scale IoT applications such as transportation, healthcare, or industrial IoT, there will be a need for networks with high bandwidth and ultra-low latency. As most IoT applications require the processing of mission-critical data, any network failure will have a huge impact on operations. For this reason, 5G will be ideal as it offers a scalable network that allows portions of bandwidth for different applications due to its network slicing method.
- Storage security and network connectivity:
Security of data is a prominent concern for organizations that are involved in IoT deployment. The IoT infrastructure is complex and vulnerable to attacks since there are multiple technologies involved. Attackers can breach into storage or sniff into the IoT network and perform malfunctions. Cybersecurity challenges also call for strong and secure network and storage infrastructure to minimize security risks.
Though the network infrastructure currently fails to meet the challenges completely, the advancements made in storage and networking technologies keep our hopes alive for better and safer IoT networks.
2. Healthcare is coming home:
A primary application of the Internet of Things to healthcare is remote health monitoring. Sometimes called telehealth, it is popular healthcare and IoT application where the patients don’t even have to visit a hospital and yet receive treatment. This not only minimizes costs but also spare some of the inconvenience of travel.
A pivotal moment that occurred in the IoT was CVS’ announcement to acquire Aetna. The announcement of acquiring Aetna demonstrates the continuation of healthcare’s journey from hospital to home. CVS has been consistent with this trend since it acquired Minute Clinic in 2006.
Another breakthrough regarding IoT and healthcare comes in the form of prescription and medication. Pills containing a microscopic sensor can send signals to an external device, usually a patch, to ensure proper usage and dosage. Such information is vital to patients who want to remember to take their prescriptions. Patients may also have access to this information via a smartphone app where they can track their performance and improve their habits.
3. KRACK reveals how IoT security can work:
The exploit of key reinstallation attacks on Wi-Fi (KRACK) was a major security event in the IoT world. While it was neither the first IoT security flaw nor the worst, still it taught the IoT developers much about IoT security. Most hack readers were able to make repairs as soon as they were informed of the situation. The use of standards within the IoT ecosystem that day showed one of the basics to good IoT security design.
IoT security will be a significant issue for a long time to come, but KRACK demonstrated that even a security breach of widely standards could be managed by those who are prepared. This leads us to an important last lesson, that is to get familiar with IoT and keep it as a top priority.
4. Keep IoT as your top priority:
This should’ve been said in 2015 or 16 when IoT was catching. By now, IT professionals should have made the transition to the IoT industry and reaping its benefits. However, it’s never too late. If you haven’t joined the bandwagon yet, take the leap now. The industry is evolving, and there is a huge demand for professionals. Luckily, with that demand, comes a plethora of educational options for those interested in the IoT field. There’s no shortage of traditional college programs, or for those that need more flexibility in their studies, consider an online degree program in data science or cybersecurity…
Currently, the number of IoT devices is increasing globally, which is generating trillions of gigabytes of data every day. Many companies are channelizing their efforts and funds to bring in precision to the Internet of Things. Top companies in Silicon Valley are investing in the IoT sector and disrupting the way we live and work. This has led to a demand for skilled IoT security and data professionals who can address the flaws of the connected devices. Similarly, there is a stark requirement for research analysts and IoT cloud architecture and other job roles that require specialized skills.
Conclusion:
While there are no two views about the growth of IoT deployment, there is still a need for proper security methodologies that can protect the network, devices and the data. It is a must for businesses to take immediate steps and profile the IoT activities because, in the words of Kevin Ashton, “It’s a world where tens of thousands of organizations are saving and making hundreds of millions of dollars from the Internet of Things, using cars that drive themselves, subway stations that sense passengers, algorithms that diagnose deadly diseases using phones, & many other once apparently impossible technologies. The future promises far more amazing things. The most important decision you can make now is how to be a part of it.”



